Clawdbot Guide: Build a Secure Self-Hosted AI Control Plane

Learn how to build a secure AI Control Plane with Clawdbot. Master self-hosted agent architecture, mitigate prompt injection risks, and discover why BrowserAct is the elite choice for web-scale automation.
In the rapidly shifting landscape of Generative AI, we are witnessing a transition from passive chatbots to proactive agents. While most people are content with the limitations of a browser-based chat window, power users are deploying Clawdbot (also known as Clawd)—a self-hosted, local control plane that treats LLMs as interchangeable modules in a larger, personal operating system.
The Core Philosophy: Why "Local Control" Matters
Clawdbot isn't just another tool; it's a Gateway. Its primary purpose is to decouple the "Thinking" (LLM) from the "Doing" (Local Execution).
- Unified Communications: Instead of checking five different apps, Clawdbot bridges Telegram, Slack, WhatsApp, and Discord into a single, AI-managed hub.
- The "Lobster" Engine: One of Clawdbot’s unique features is its deterministic execution layer. While pure LLMs are prone to "hallucinating" file paths or shell commands, the Lobster engine enforces a structured workflow that is both auditable and recoverable.
- Agentic Persistence: Unlike standard AI sessions that reset, Clawdbot maintains a Long-term Memory and supports Cron-based proactive tasks (e.g., "Summarize my unread emails every day at 8 AM").
Technical Architecture: How the "Brain" Meets the "Machine"
Understanding the flow is crucial for anyone looking to implement this system securely.
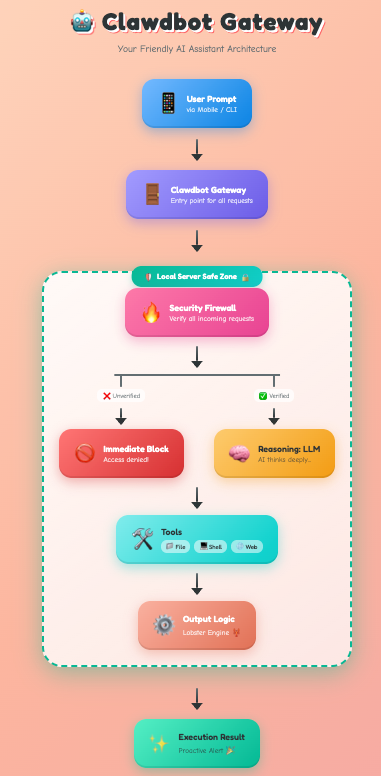
The Execution Journey:
- Ingress: A command arrives from a remote CLI or a mobile app like Telegram.
- Firewall Logic: The system immediately validates the Pairing Code. This is the first line of defense against unauthorized access.
- Reasoning Engine: The prompt is sent to the LLM (Claude/GPT) along with local context (recent files, user preferences).
- Deterministic Action: The "Lobster" engine translates the LLM's intent into safe, executable steps—whether that's a Python script, a Shell command, or a Web search.
- Egress: The result is pushed back to the user, and the interaction is logged for long-term memory.
Deep Dive: The Hidden Risks of Self-Hosting AI
With great power comes significant system-level risk. Clawdbot’s ability to execute Shell commands is a "double-edged sword."
- The Prompt Injection Threat: A "jailbroken" prompt from a compromised channel could potentially instruct your AI to delete directories (
rm -rf) or exfiltrate your.sshkeys. - Infrastructure Fatigue: Running a self-hosted gateway requires 24/7 uptime. For most, this means managing a VPS, handling SSH Tunnels (Tailscale/Cloudflare), and constant Node.js environment maintenance.
- Token Overhead: Automated "loops" (where the AI keeps trying a task until it succeeds) can result in an unexpected surge in API costs if not strictly capped.
Scaling Up: When to Move to BrowserAct
While Clawdbot excels at Local Data Governance, it often hits a wall when dealing with the Complex Web. If your workflows involve heavy web scraping, price monitoring, or interacting with highly protected platforms, the local approach becomes fragile.
This is where BrowserAct provides the professional-grade extension your AI agent needs.
Comparison: Clawdbot vs. BrowserAct
Feature | Clawdbot (Self-Hosted) | BrowserAct (Cloud-Native) |
Best For | Local file management & Terminal tasks | Web-scale data extraction & Market Intelligence |
Security | Local risk; requires VM/Sandbox | Isolated Cloud Sandboxes (Total safety) |
Web Success Rate | Low (Blocked by CAPTCHAs/IP bans) | High (AI-Native Anti-bot & Residential IPs) |
Maintenance | High (Server/Node.js/Tunnels) | Zero (Ready-to-use API) |
Scalability | Limited by local hardware | Unlimited Cloud Parallelism |
Strategy: The Hybrid Approach for 2026
For the ultimate setup, SEO experts and developers are adopting a Hybrid AI Strategy:
- Use Clawdbot for high-privacy tasks: Managing local code repositories, organizing personal documents, and running local system diagnostics.
- Integrate BrowserAct for all "Outbound" intelligence: Let BrowserAct handle the dirty work of the web—bypass anti-bot systems, solve CAPTCHAs, and gather structured data from the internet.
By delegating web interaction to BrowserAct, you eliminate the risk of exposing your home IP and ensure your automation workflows never break due to a simple website update.
Summary: Building a Future-Proof Agent
The era of manual browsing is ending. Whether you choose the rugged autonomy of Clawdbot or the streamlined power of BrowserAct, the goal is the same: reclaim your time through agentic automation.
Ready to supercharge your AI's web capabilities?

Relative Resources

Everyone Is Talking About Clawdbot (Moltbot). Here’s What’s Real

Why Clawdbot Wins: Gateway Architecture, Permissions, Risks

Clawdbot (Moltbot): What Siri Was Supposed to Be

ClawdBot: The Open-Source Personal AI Agent That's Taking Silicon Valley by Storm
Latest Resources

Is ClawdBot Safe? Security Risks Every CEO Must Know in 2026

Clawdbot Viral: How to Deploy 24/7 AI Powerhouse in One-Click

Why Clawdbot Changed Its Name to Moltbot
